UPDATE: I contacted my ISP about this app. They noted that during the install process there's a 'BEGIN' button with text under it that says 'By tapping "begin" you accept our EULA. I don't think it sufficiently covers what they are doing still. The app's name is RouteThis.
Beyond this, their response is as follows "If you no longer wish to use the RouteThis application, you can cease using this and uninstall the application at any time."
I've been having packet loss issues recently and my ISP asked me to run an app as a part of their troubleshooting process.
Immediately alarm bells start ringing as the app proceeds to do 'things', sends them information, and then doesn't tell you what it sent them.
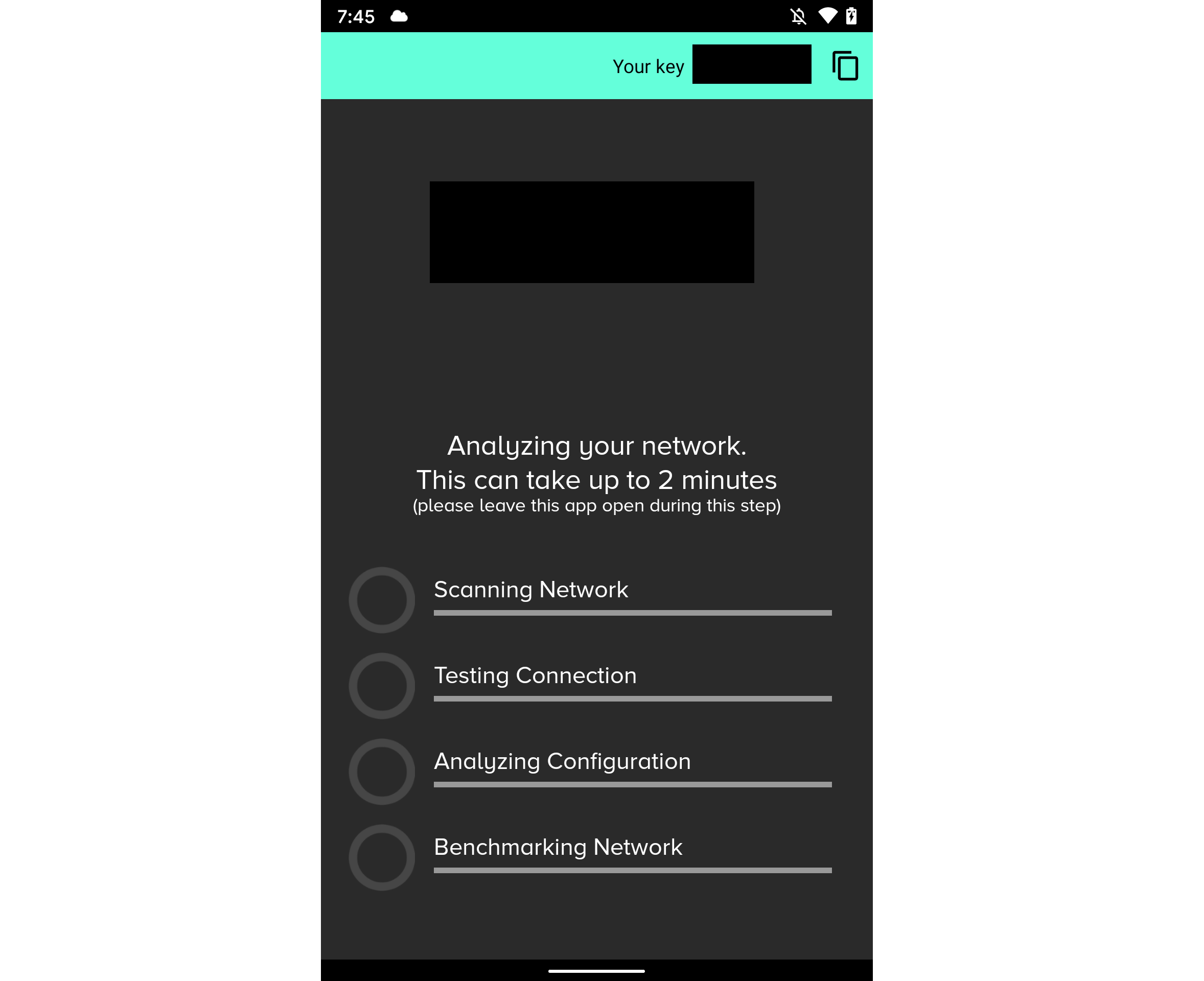
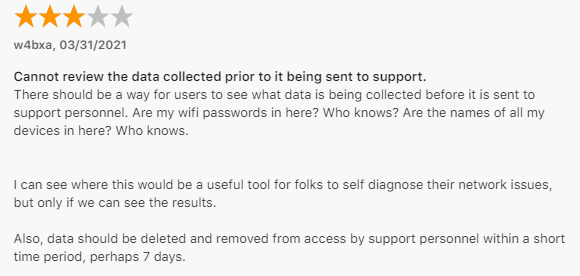
Reading the reviews from the app store I see I'm not the only one with these concerns.
So I decided to have a peek for myself to figure out what I'd just sent them.
Their Claims
First off let's have a look at what they say they actually collect and why. From their privacy policy:
REDACTED collects the following information: information on the End User’s home network, location information, IP Address, MAC address, devices on their network, screenshots of their router, devices on their network, surrounding Wi-Fi networks, make/model of router, network topology, amount of bandwidth being consumed on network, type of mobile phone, speed test, connection quality to various devices both inside and outside the customer’s home, port tests, traceroutes, ping tests, DNS lookups, multicast configuration (“Network Information”).
Now why do they need all this? The only relevant dot point in their privacy policy is listed below.
Assess network strength and diagnose connectively or other technical issues on behalf of our Customer;
Looking at their LinkedIn page for a bit more context the solution seems to focus on resolving ISP tickets by ruling out the end user's WiFi being the problem.
Fair enough.
Trust but Validate
To validate what the app is actually doing I ran a packet capture and had all HTTP/s traffic from my phone proxied through Burp.
Immediately it's clear that the app is highly configurable. The first thing the app does is pull a configuration file which tells it what to do. I'll paste some of the more interesting snippets of configuration below.
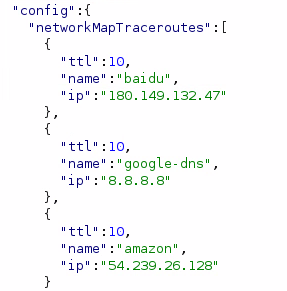
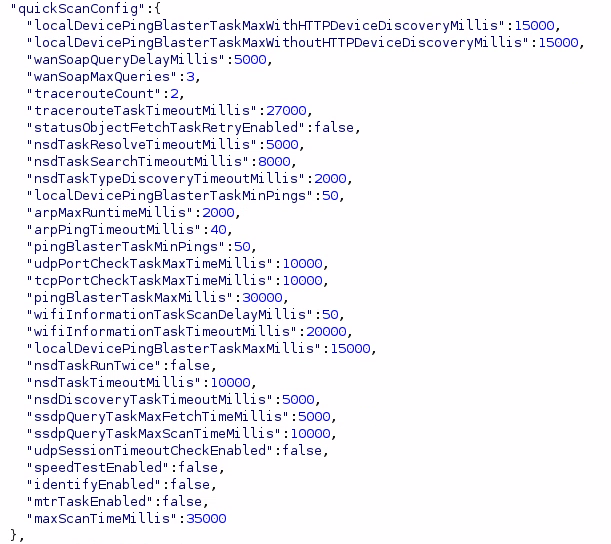
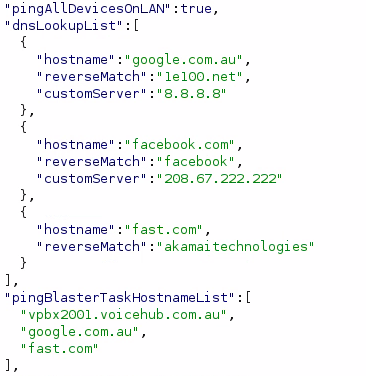
As I scroll through this catches my eye...
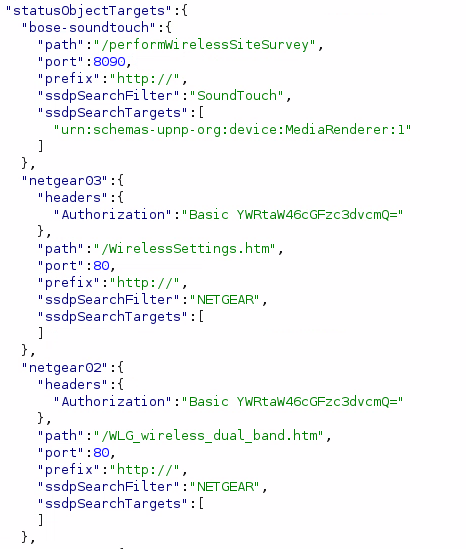
It looks like the application has a bunch of preconfigured device definitions which it will try to pull data from.
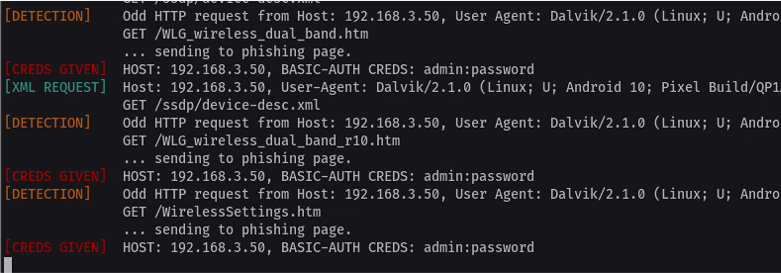
More worryingly, if you have a device that advertises a SSDP device type containing the word NETGEAR, it will try to get to login using the username of admin and a password of password.
Trying to login to devices on my network using default credentials seems like an overreach beyond just collecting information about 'devices on the network'.
To confirm this behaviour I configured my Kali box to be discoverable via SSDP with a device type of NETGEAR using evil-ssdp and then ran the scan again.
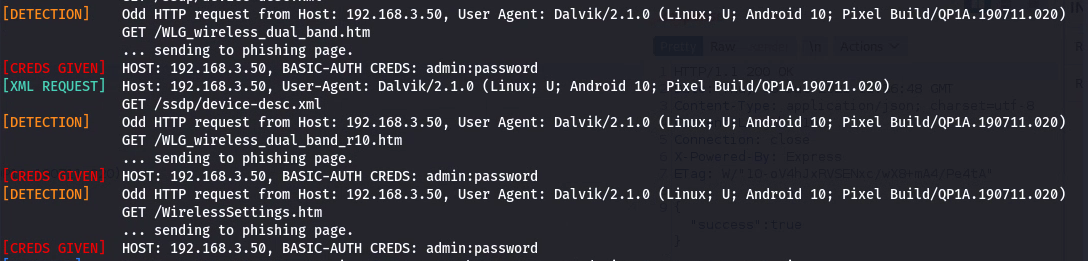
As expected, the lines in red are my phone trying to login to the fake page hosted on my Kali server.
It'll then send whatever response contents it gets back from these requests back off to their servers (ignore the response sent in my example, it's a generic 365 template from evil-ssdp).
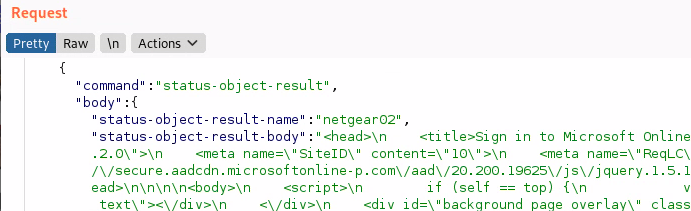
Change your default passwords people!
The Full List of Tasks Observed in My Run
Beyond this I figured I'd also document the full list of checks for the interested individuals.
- NetworkMapTracerouteTask
- HNAPInformationTask
- WifiInformationTask
- DNSLookupTask
- NsdServiceDiscoveryTask
- SSDPTask
- BroadcastDiscoveryTask
- ARPDiscoveryTask
- RouterDetailsTask
- TracerouteTask
- RouterHTTPTask
- SpeedtestTask
- ConnectivityCheckTask
- TCPPortCheckTask
- UDPPortCheckTask
- NsdTask
- ARPHostnameQueryTask
- HTTPDeviceDiscoveryTask
- PingBlasterTask
- StatusObjectFetchTask
- WANSOAPTask
- LocalPingBlasterTask
Conclusion
End users who come across this application should consider running the app with your phone connected to your Guest network if you have one.
For the company that makes this software and my ISP my notes are below:
- Logging into my devices without consent is not cool.
- The application should request end users to accept their privacy policy prior to proceeding.
- The application should give end users the option of reviewing what's being sent.